Topics
Threats in networks
Network Security Controls – Architecture, Encryption, Content Integrity, Strong Authentication, Access Controls, Wireless Security, Honeypots, Traffic flow security.
Firewalls – Design and Types of Firewalls, Personal Firewalls, IDS
Email Security – PGP, S/MIME
Threats in Network
Threat - Potential vulnerability that can breach security and negatively alter, erase the data or can have unwanted impact on computer system.
Malware - Malicious + Software. All are malicious software but behaves differently.
On the basis of Infection
-
Virus – Self Replicating, hooks on a program, can travel all over the internet and infect a computer without permission of the user… The Creeper Virus was first detected on ARPANET.
-
Worms – Self Replcating, don’t hook on computer, are network-aware(can travel in network). Don’t do much harm rather consume hard disk space thus slowing down the computer.
-
Trojan – Conceal themselves inside the software that seem legitimate and it is executed when required. Used often provide backdoor gateway for malicious programs to enter your system and steal your valuable data without your knowledge and permission. Examples include FTP Trojans, Proxy Trojans, Remote Access Trojans(RAT) etc.
-
Bots –: Automated processes that are designed to interact over the internet, without the need for human interaction. Malicious bot can infect one host and after infecting will create connection to the central server which will provide commands to all infected hosts attached to that network called Botnet.
Malware on the basis of Actions:
Shikari par ASR ZR Sanya ka
-
Adware – Not malicious. Breach user privacy to display ads. Come attached with free-to-use software. Monitor user’s interests and display relevant ads.
-
Spyware – Monitors computer activity on computer and share the collected information to an interested party. Generally dropped by Trojans. Sits silently to avoid detection. Most common example - KEYLOGGER.
-
Ransomware – Will either encrypt your files or will lock your computer making it inaccessible either partially or wholly. Then a screen will be displayed asking for money i.e. ransom in exchange.
-
Scareware – Masquerades as a tool to help fix your system but when executed it infects system completely.
-
Rootkits – Gain root access or administrative privileges in the user system.
-
Zombies – similar to Spyware, except wait for hacker’s command.
2. Network Security Controls
Introduction
-
Ensures the CIA (Confidentiality, Integrity, Availability) of network services. by implementing either technical or administrative safeguards implemented to minimize the security risk.
-
To reduce the risk of a network being compromised, an adequate network security requires implementing a proper combination of network security controls.
Encryption

Strong Authentication(13)
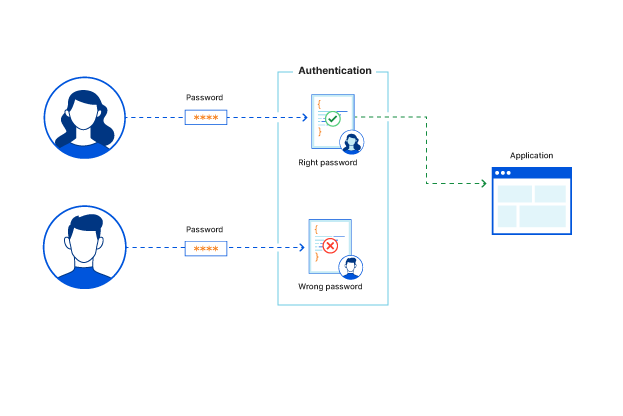
Access Control
Limiting access of computer resources to users. This mechanism grants access(read, write, execute) to the user/application based on the access permissions and their associated roles.
Includes : CRUD(Create , Read , Update , Delete) of File permissions, Execution of Program permissions, Data rights to retrieve or update information in a database.
Types
1. Discretionary Access Control (DAC)
Owner of the resource decides how it can be shared. He himself responsible to give read/write access to others.

2. Mandatory Access Control (MAC)
User works in a company and the company decides how data should be shared like Hospital owns patient records and limits their sharing. For example HIPAA for health information
In short, who can share what and to whom.
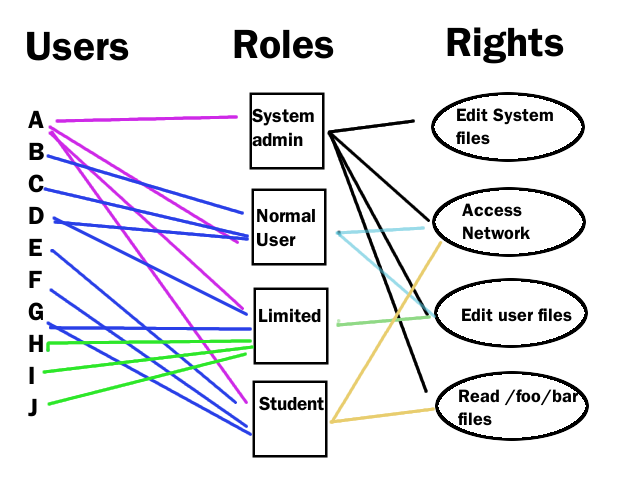
3. Role Based Access Control (RBAC)
It is not based on users, rather it is based on Roles. What you are performing you will have the access to it.
Identification: Confirming the user’s identity, process or device accessing the network, via unique User ID/Acc Number.
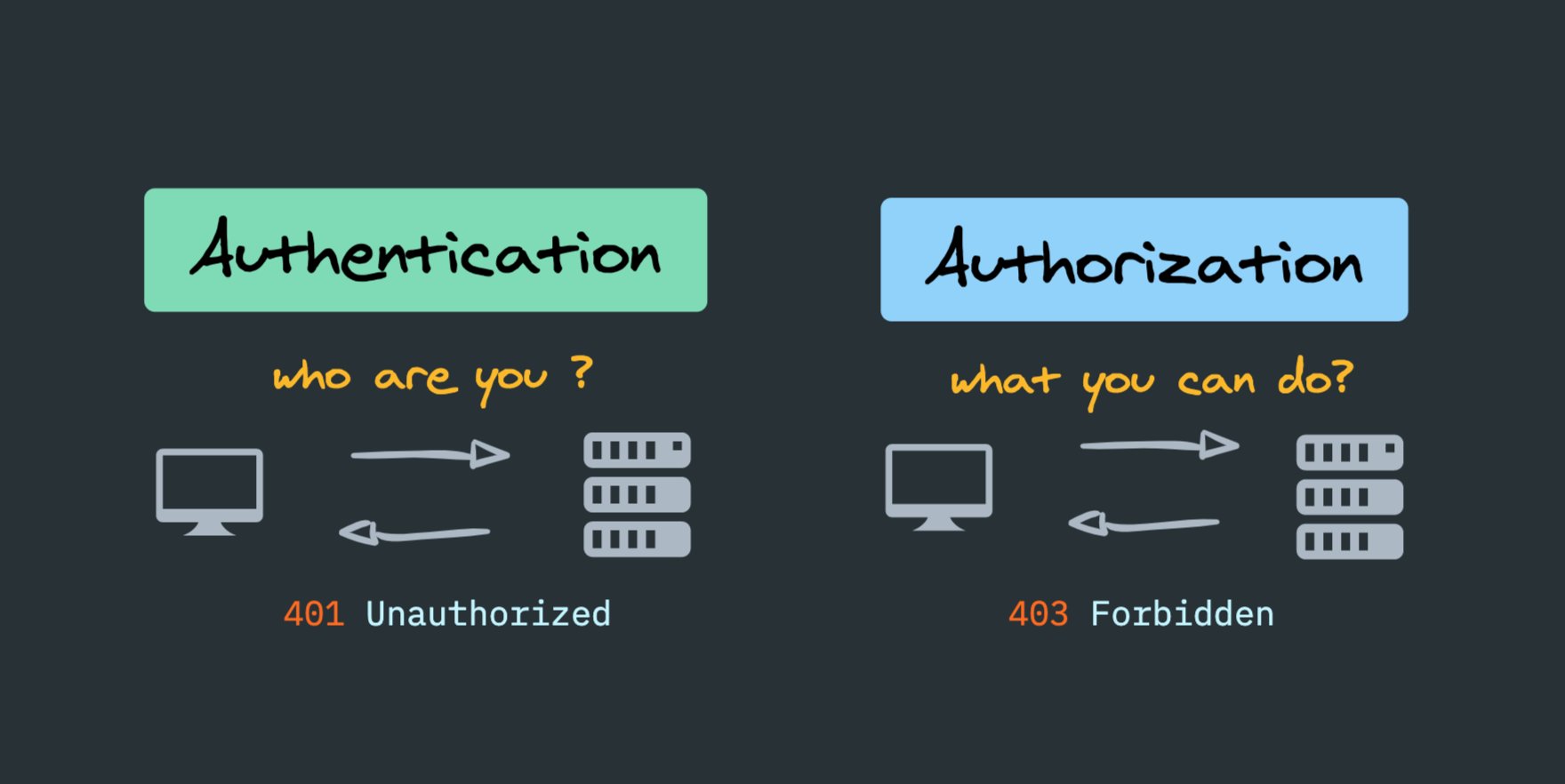
Authentication: Who are you ? Verifying the credentials provided by the user while attempting to connect to a network. A typical user authentication consists of a user ID and a password.
Authorization: What action a user can perform. What you can do ?
Accounting Tracking the actions performed by the user on a network. It keeps track of who, when, how, what the users access the network. It helps in identifying authorized and unauthorized actions.
Wireless Security
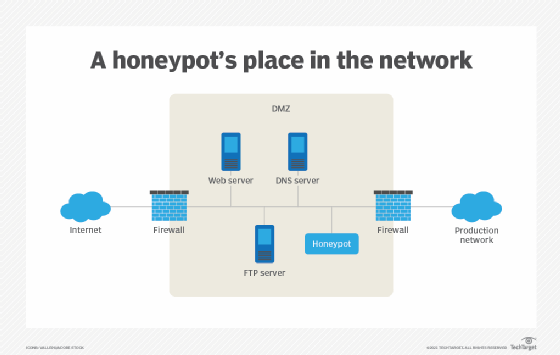
Honeypots
- A network-attached system used as a trap for cyber-attackers to detect and study the types of attacks used by hackers.
- It acts as a potential target on the internet and informs the defenders about any unauthorized attempt to the information system.
- Mostly used by large companies and organizations.
- The cost of a honeypot is generally high because it requires specialized skills and resources to implement.
- A honeynet is a combination of two or more honeypots on a network.
Classified based on their deployment and the involvement.
-
Research honeypots- These are used by researchers to analyze hacker attacks and deploy different ways to prevent these attacks.
-
Production honeypots- Production honeypots are deployed in production networks along with the server. Act as a frontend trap.
Based on interaction
- Low interaction honeypots: Gives little insight & control to the hacker about the network. It simulates frequently requested services.
- Medium Interaction Honeypots: Certain activities and are designed to give certain responses.
- High Interaction honeypots: Large no. of services, trying to get complete information about the hackers.
Traffic Flow Security
Hide the traffic levels across an IT infrastructure.
The idea behind traffic-flow security is to make it impossible for external observers to see whether traffic is changing in real time, or when any individual message goes from one location to another.
Methods - Use dummy traffic, Encrypt actual messages. Send a continuous encrypted signal even when a network is not being used.
Necessary to hide traffic on a platform where knowledge of access times and traffic levels could be used inappropriately by an outside observer.
2. Firewalls
Introduction
- A network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules it accepts, rejects or drops that specific traffic.
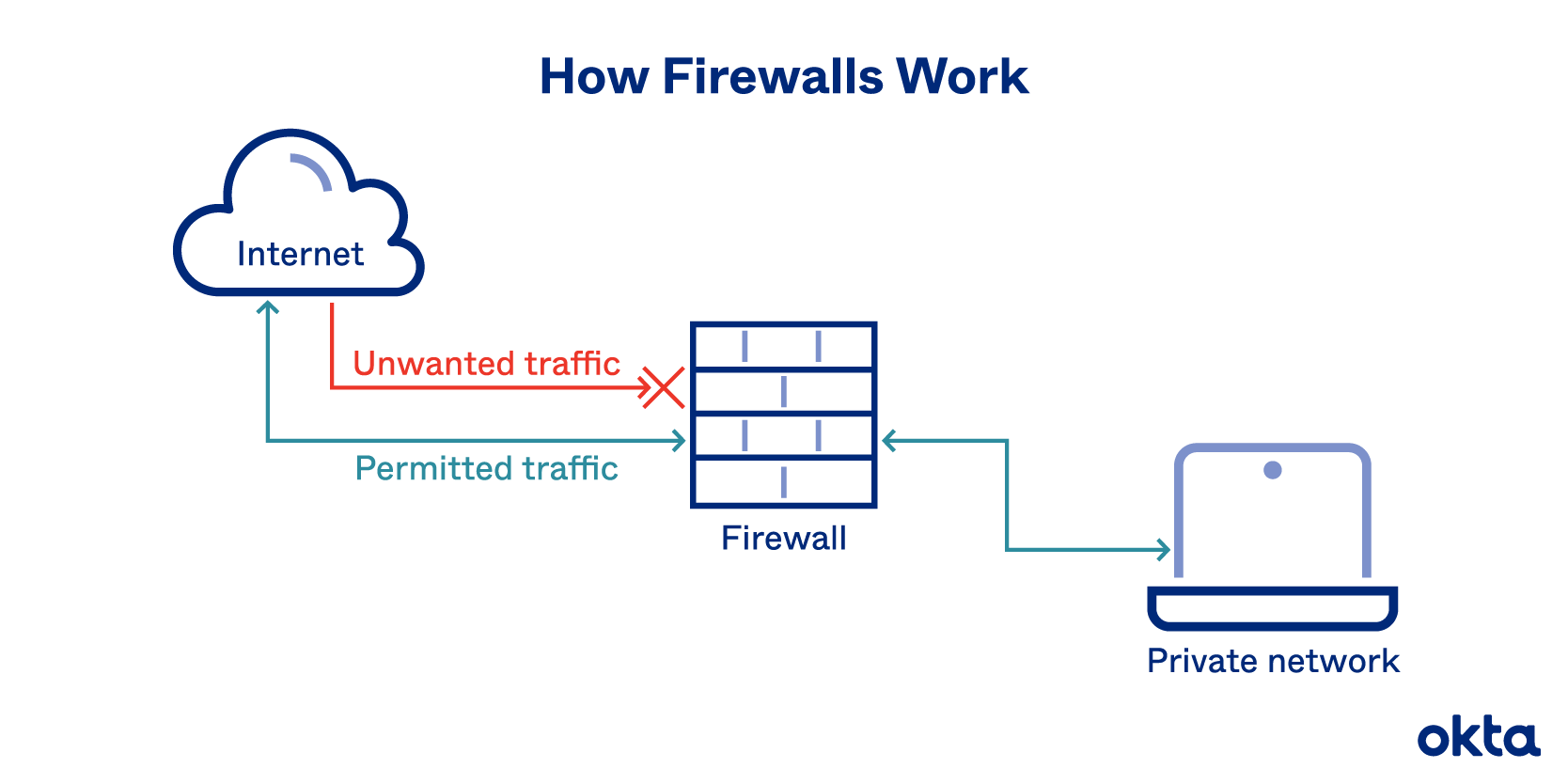
Working
Firewall matches the traffic against the rule set defined in its table. Once the rule is matched, associate action is applied to the network traffic.
For example, HR department cannot access the data from code server and system administrator can access the data from both HR and technical department.
Outgoing and Incomming Traffic rules are set separately.
Default policy: It is very difficult to explicitly cover every possible rule on the firewall. For this reason, the firewall must always have a default policy. Default policy only consists of action (accept, reject or drop).
If default policy on the firewall is set to accept, then any computer outside of your office can establish an SSH connection to the server. Therefore, setting default policy as drop (or reject) is always a good practice.
Design
Requirements, Outlining Policies, Deployment Location
Types of Firewalls

-
Host- based Firewalls : Host-based firewall is installed on each network node which controls each incoming and outgoing packet. It is a software application or suite of applications, comes as a part of the operating system. Host-based firewalls are needed because network firewalls cannot provide protection inside a trusted network.
-
Network-based Firewalls : It works on network level. In other words, these firewalls filter all incoming and outgoing traffic across the network. It protects the internal network by filtering the traffic using rules defined on the firewall. A network-based firewall is usually a dedicated system with proprietary software installed, or might have two or more network interface cards(NIC).
-
Packet Filtering – Also known as static firewall. Monitors outgoing & incoming packets thus pass or halt based on the source and destination Internet Protocol (IP) addresses, protocols, and ports.
-
Stateful Inspection– Also called dynamic packet filtering. Monitors how data packets move through a firewall and Inspect that if the packet belongs to a particular session or not. Block if not.
-
Application Level Gateway – Also called Proxy Firewall. Examine application layer information like an HTTP request. If finds some suspicious application it gets blocked right away.
-
Next-generation Firewalls – Also called intelligent firewalls. Performs all the task performed by firewalls mentioned above, with additional features like application awareness, intrusion prevention, and cloud-delivered threat intelligence.
-
Circuit-level gateways – A circuit-level gateway is a firewall that provides User Datagram Protocol (UDP) and Transmission Control Protocol (TCP) connection security.
-
Software Firewall – Type of computer software that runs on our computers. It protects our system in real time by notifying us about the danger if occur.
-
Hardware Firewall – Physical appliance that is deployed to enforce a network boundary.
-
Cloud Firewall – FaaS(Firewall As A Service). Cloud-deployed network devices. Unlike traditional firewalls, a cloud firewall filters data at the cloud level.
Personal Firewalls
A software application that shields internet users from potential hackers by permitting or denying network traffic to and from their computer and warning them about attempted intrusions. It’s like a filter between the Internet and your network.
Example : McAfee LiveSafe, Kaspersky Internet Security, Bitdefender Internet Security.
IDS
Introduction
Intruder(person who tries to gain unauthorized access over network with criminal intention) - Intrusion - IDS(Intrusion Detection System)
Outside Intruder(Masquerader)
Inside Intruder(Misfeasor) - Misusing the privelleges granted. “Dagabaazz”

Methods
- Signature Based IDS - Detect attacks comparing with database of attack pattern. Cannot identify new attack.
- Anamoly Based IDS - System Administor sets the access to various roles. Deviation from normal behaviour/base line.
Classification
- NIDS(Network Based) - Deployed within a network to Monitors, Capture, Analyze network traffic continuously and detects malicious data packets. How - Matches the traffic with library of known attacks. Very difficult to analyse in big and busy network.
- HIDS(Host Based) - Installed on individual host or device network. Monitors data packets from device only. How - Snapshot, comparing existing system with previous system checking files detected or modified.
- PIDS(Protocol Based) - Monitoring HTTPS protocol stream.
- APIDS(Application Protocol Based) - Identifies the intrusions by monitoring and interpreting the communication on application-specific protocols. SQL protocol detection as middleware.
- HIDS(Hybrid) - host agent or system data is combi/ned. Prelude
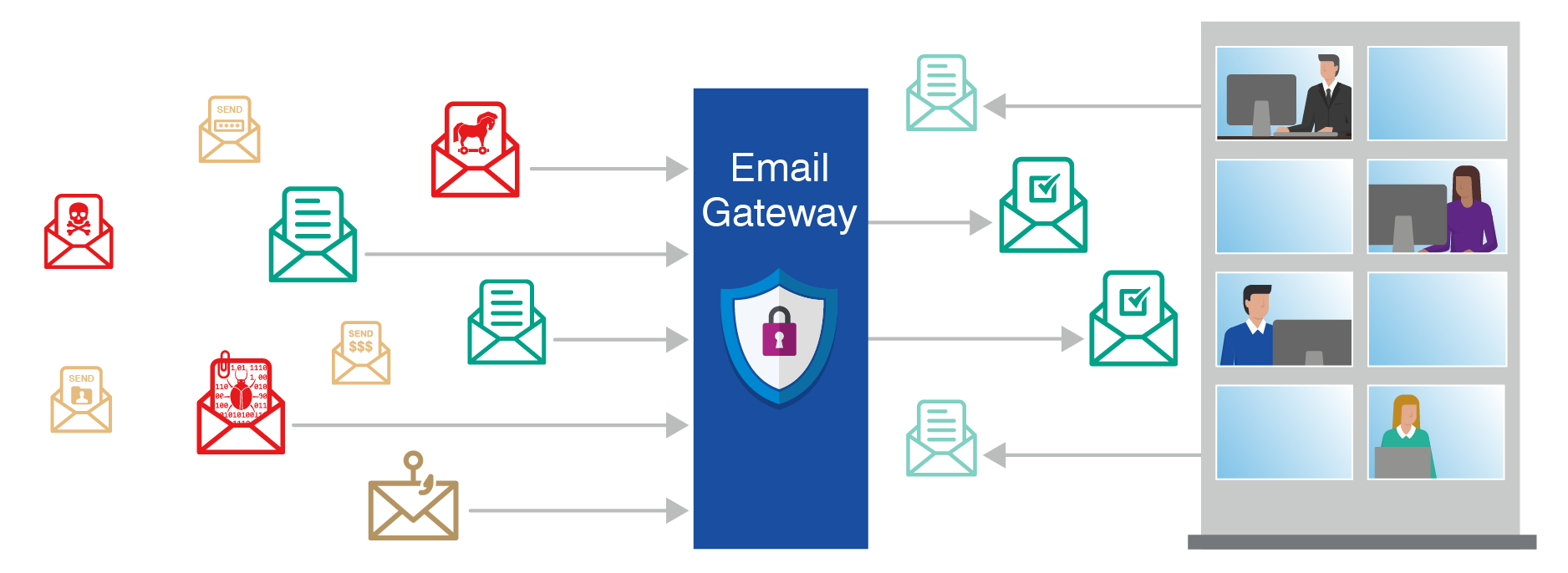
3. Email Security
Definition
- Techniques for protecting email accounts, (acc mey kya hai) content, and communication(karta kya hai) against unauthorized access, loss, compromise (each one above) and to prevent the spread spam and phishing attacks.
Why
- Email is open and accessible as possible. Thus, the security of email, on its own, is not reliable.
- Hence, attackers try to take advantage of the lack of email security to carry out their attacks. Commonly attackers use deceptive messages to entice recipients and to gain sensitive information.
- Since most organizations rely on email to do business, attackers exploit email in an attempt to steal sensitive information.
Common Attacks
- Phishing: When a fake webpage is sent to victim to collect credentials.
- Malware: Deliverin spyware, scareware, adware via email, or any other malicious code.
- Account takeover: Attackers take over email inboxes from legitimate users.
- Email interception: Attackers can intercept emails in order to steal or monitor the information they contain.
Common Preventions
- Email security policies as removing executable content from emails.
- Sending suspicious content to a sandboxing tool for detailed analysis.
- Implementing automated email encryption.
- One of the first best practices is implementing a secure email gateway (It scans and processes all incoming and outgoing email) and makes sure that threats are not allowed in.
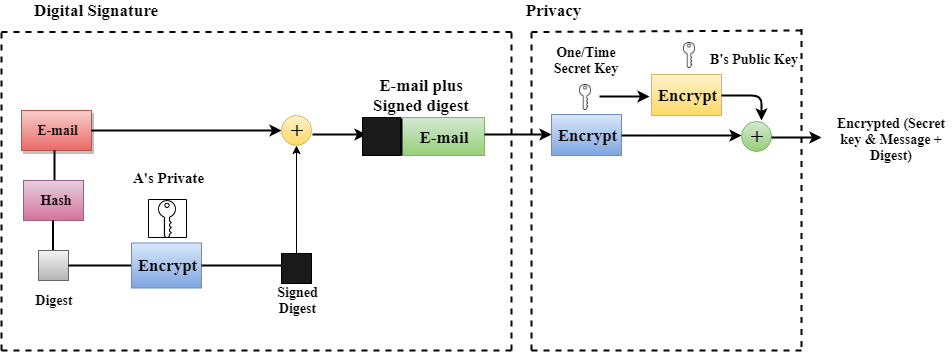
PGP
Introduction
- PGP stands for Pretty Good Privacy, invented by Phil Zimmermann.
- Designed to provide four security aspects i.e., Privacy, Integrity, Authentication, and Non-Repudiation in the sending of email. 🚀PIAN
- It is Open source and freely available software package for email security.
- It provides compression by using the ZIP algorithm, and EMAIL compatibility using the radix-64 encoding scheme.
Working
Uses one hash function, one secret key, and two private-public key pairs.
Sender (A)
Reciever (B)
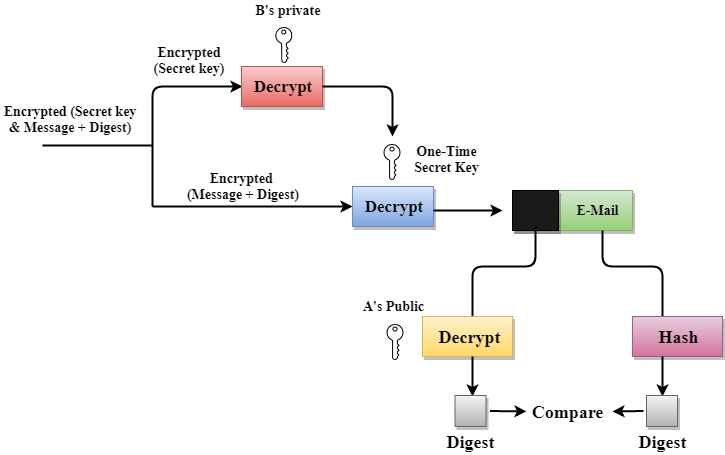
Advantages
- Integrity - H
- Privacy & Authentication - B’s Public Key
- Non-Repudiation - This System
- PGP provides authentication through the use of Digital Signature.
- Provides confidentiality through the use of symmetric block encryption.
- Combination of secret key encryption and public key encryption to provides privacy.
- Very strong encryption.
Disadvantages
- Admin Issues The different versions of PGP complicate the administration.
- Compatibility issues Both the sender and the receiver must have compatible versions of PGP. Both having different version, can’t be read.
- Complexity PGP is a complex technique, hybrid approach that implements symmetric encryption with two keys. Less familiar than the traditional symmetric or asymmetric methods.
- No Recovery: No forget password. PGP does not offer such a special program for recovery; encryption methods are very strong so, it does not retrieve the forgotten passwords results in lost messages or lost files.
S/MIME
Introduction
- Stands for Secure/ Multipurpose Internet Mail Extensions (S/MIME).
- A standard that adds an additional layer of security and encrypts the data shared via email, uses cryptography to digitally sign and encrypt to prevent unauthorized access to the data in the email.
Two Features
Includes two security features:
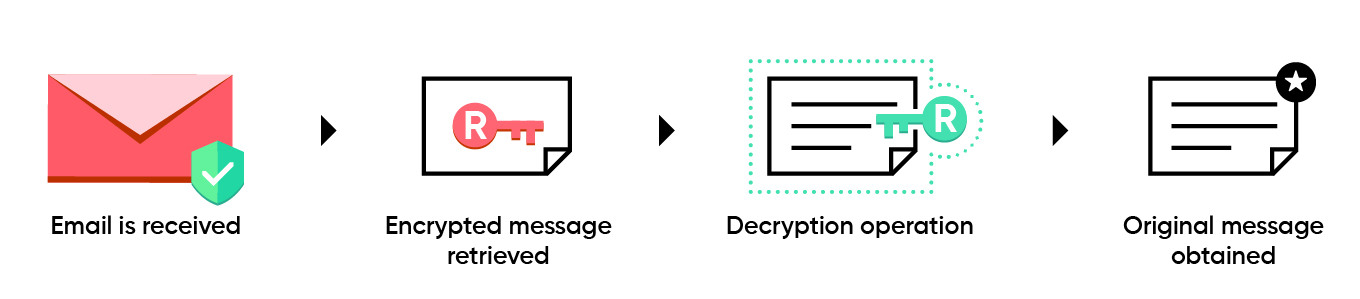
- Message Privacy & Integrity(Via Encrypting Emails) - Encrypted emails are readable only by the intended recipient.
Encryption using recipient’s public key.
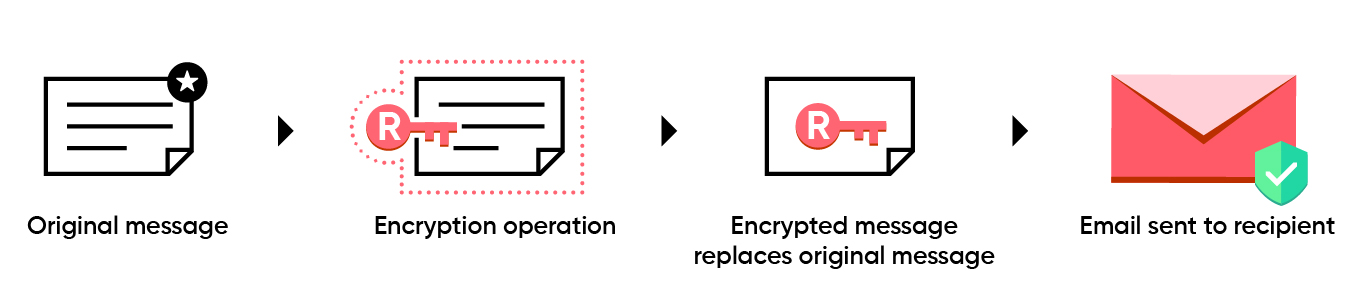
Decryption using recipient’s private key.
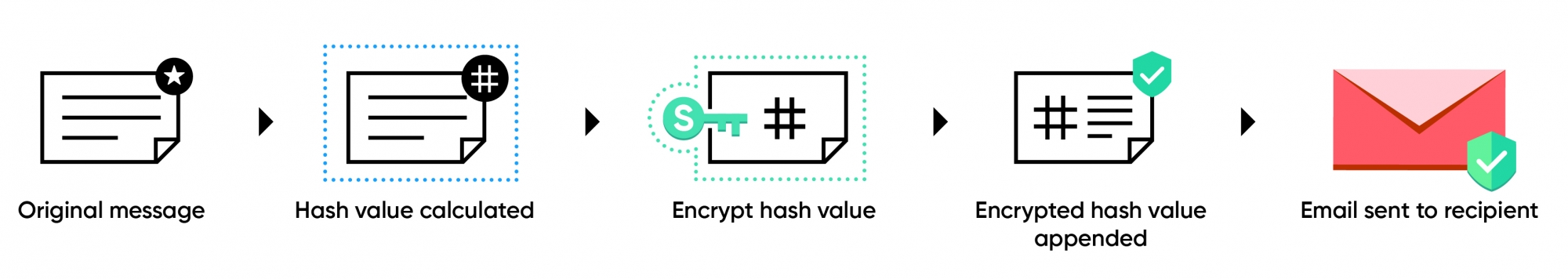
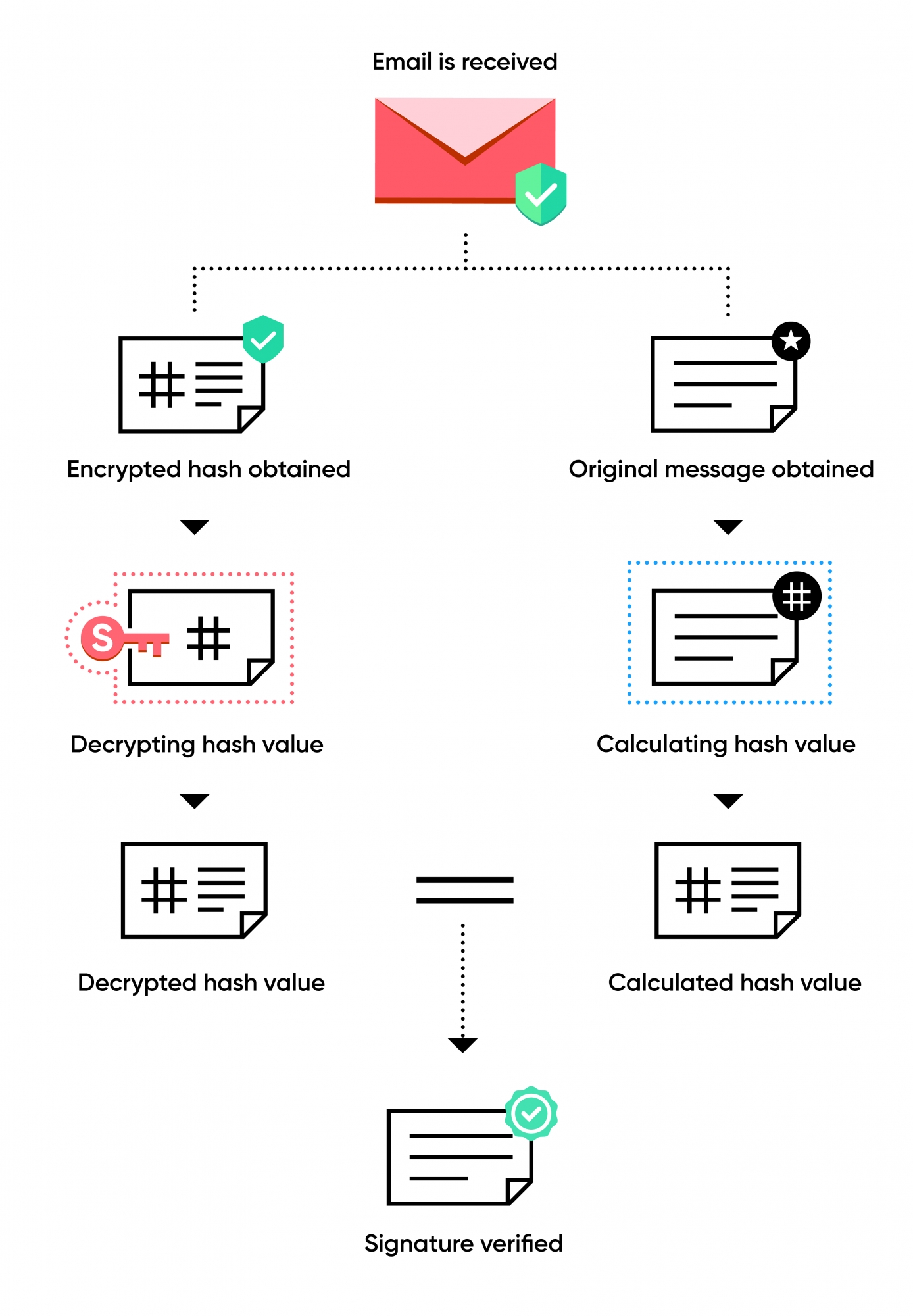
- Digital Signature - It is to validate the sender, it digitally signs the emails sent between two S/MIME enabled users to eliminate any risk of spoofing.
Sender Validation - Digital signatures are unique to each user. Thus, it allows the recipient to verify if the email is actually sent by the person who it appears from. This eliminates the risk of anyone spoofing of your email address.
Non-Repudiation - The uniqueness of the digital signature ensures that the author of the email will not be able to deny ownership of the emails. Claims of impersonation can easily be refuted.
PGP vs S/MIME
Stands for.
Diffie Hellman | Elgamal digital signature is used.
Costlier | Cheaper
4096 | 1024 Public Keys
Protexts text message | data as well.
Comments
Post a Comment