Topics
Message Authentication Requirement, Functions,
Message Authentication Code, Hash Functions, Security Of Hash Functions And Macs,
MD5 Message Digest Algorithm, Secure Hash Algorithm,
Digital Signatures. Key Management : Key Distribution Techniques, Kerberos.
Authentication Requirement & Functions
Message Authentication is to check integrity of a message, which is verifying if message received or delivered is correct & unaltered.
Security Requirements
Below are the reasons why do we need authentication.
Mnemonic DMTM kaaR
- Disclosure : Release of message.
- Masquerade : Insertion of messages from fraudulent source.
- Traffic Analysis : Identifying network traffic patterns.
- Modification in Content/Sequence/Timing : CRUD/Order/Delay.
- Source/Destination Refusal : When the source denies being the originator and receiver denies being the recipient of a message.
Authentication Functions
It is achieved by authenticator, which is generated by authentication functions.
Message Encryption : Plain Text—Cipher Text (authenticator)
Message Authentication Code (MAC) : Public function of message and a secret key is used. C(M, K) = Fixed Length Code, called MAC (authenticator).
Hash Functions (H) : A public function that maps a message of any length into a fixed length hash value. Similar to MAC, instead of key, public hash function is used. H(M) = Fixed Length Code(h). h(authenticator)
Message Authentication Code
- Message Authentication Code (MAC) used to combine message with shared secret key.
- Used to guarantee integrity AND authentication.
- Still a requirement for symmetric keys.
- Examples : HMAC-SHA1, HMAC-SHA256, HMAC-SHA512

Hash
- Hash algorithms are used to take a large message and produce a unique short digest of it.
- Used to guarantee the integrity of data.

Features
- Different data (usually) maps into different digest values. Thus, it is hard have the same hash value for two different data.
- Modification in data = Change in hash.
- Examples : MD-5, SHA-1, SHA-256, SHA-512
MD5
Introduction
- Ronald Rivest developed this algorithm in 1991.
- Accepts a message of any length as input.
- Generates a 128-bit digest (output) from a string of any length.
- Represents the digests as 32 digit hexadecimal numbers.
Features & Use Cases
- A minor change in the input string generate a drastically different digest.
- Use cases : Password Verification, File Download to check hashes.
Steps
- Append Padding Bits : The size is 64 bits short of a multiple of 512,
512x - 64. When it comes to padding the bits, it must be one(1) followed by zeros(0).

- Append Length Bit : To make the final string a multiple of 512, take the length of the initial input and express it in the form of 64 bits. Thus, we can represent a message of length 2^64.

Example :
Original message is: 1000 bits.
Padding bits added: 472
Total Length is : 1472
If we add 64 to 1472, we get 1536, which is multiple of Activate 512(512X3=1536)
- Initialize MD buffer : Four different buffers, namely A, B, C, and D, 32-bits each are initialized as follows:
A(HEX) = 01 23 45 67
B(HEX) = 89 ab cd ef
C(HEX) = fe dc ba 98
D(HEX) = 76 54 32 10

- Process Each Block : For each block, a total of 64 operations are performed in 4 Rounds, each round having 16 operations using functions are
F,G,H,I. Resulting 32 bit output taking B, C, D as input.

F : Round 1: (B ∧ C) v (~B ∧ D)
G : Round 2: (B ∧ D) v (C ∧ ~D)
H : Round 3: B ⊕ C ⊕ D
I : Round 4: C ⊕ (B v ~D) 👁️
To perform the operations, we need the following
add modulo 2^32
M[i] – 32 bit message, 16 input sub-blocks, named M[0], M[1] ... M[n]
K[i] – 32 bit constant, array of 64 constants.
<<<n – Left shift by n bits.

Secure Hash Algorithm
- Developed by NIST & NSA.
- Accepts a message of any length as input, but SHA-256 takes input message size < 2^64-bits.
- Generates a 160-bit digest (output) from a string of any length.
- Represents the digests as 40 digit hexadecimal numbers.
- SHA versions SHA-0/1/2/3/4
- Designed primarily to make infeasible to obtain the original message given its digest and infeasible to find two messages producing the same digest.
Working
- Pre-processing is same.
- Machine have 1 box more.
E(HEX) C3 D2 E1 F0
Total of 80 operations in 4 rounds, each round having 20 operations.

Round 1: (B ∧ C) v (~B ∧ D)
Round 2: B ⊕ C ⊕ D
Round 3: (B ∧ C) v (B ∧ D) v (C ∧ D)
Round 4: B ⊕ C ⊕ D 👁️

Key Management
Key management supports key generation, distribution, destruction, storage, backup and maintenance of the key between authorized users.
Why : If the key is known to the third party then the whole security mechanism becomes worthless.
Key Distribution Techniques

Distribution of Public/Asymmetric Key
1. Public Announcement: PK is broadcasted to everyone. A drawback is Forgery (Anyone can create a key claiming to be someone else and broadcast it.) Whom to trust ?

2. Publicly Available Directory: PKs are stored in a public directory. Directories are trusted here, with properties like Participant Registration, access and allow modifying values at any time, contains entries like {name, public-key}. You can trust.
3. Public Key Authority: It is similar to the directory but, improves security by tightening control over the distribution of keys from the directory. . Whenever the keys are needed, real-time access to the directory is made by the user to obtain any desired public key securely. You difficultly distribute.
4. Public Certification: This time authority provides a certificate (which binds an identity to the public key) to allow key exchange without real-time access to the public authority each time. The certificate is accompanied by some other info such as period of validity, rights of use, etc. All of this content is signed by the private key of the certificate authority, and it can be verified by anyone possessing the authority’s public key.
First sender and receiver both request CA for a certificate which contains a public key and other information and then they can exchange these certificates and can start communication.
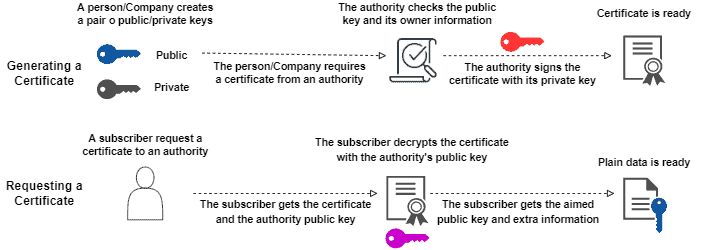
Symmetric Key distribution using asymmetric encryption
Because of the inefficiency of public-key cryptosystems, they are almost never used for the direct encryption if sizable blocks of data, but are limited to relatively small blocks. One of the most important uses of a public-key cryptosystem is to encrypt secret keys for distribution.
Digital Signature
- A digital signature is an electronic, encrypted, stamp of authentication on digital information such as email messages, macros or electronic documents.
- A signature confirms that the information originated from the signer and has unaltered.
Kerberos
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users.
Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
The main components of Kerberos are:
-
Authentication Server (AS): Performs the initial authentication and ticket for Ticket Granting Service.
-
Database: AS Verifies the access rights of users in the database.
-
Ticket Granting Server (TGS): Issues the ticket for the Server.
Kerberos Overview:
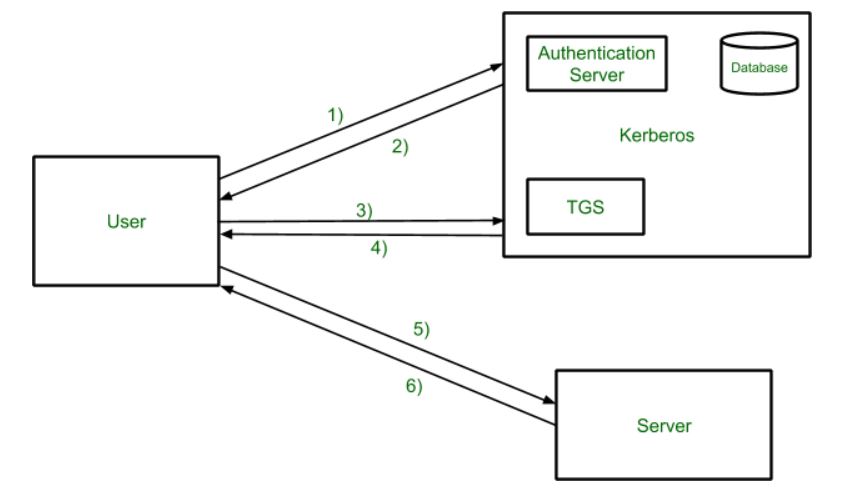
-
ASverifies user’s access right using database and then gives ticket-granting-ticket and session key. Results are encrypted using the Password of the user.
-
The decryption of the message is done using the password then send the ticket to Ticket Granting Server.
-
The user sends the Ticket and Authenticator to the Server.
-
The server verifies the Ticket and authenticators then generate access to the service. After this User can access the services.
Is Kerberos Infallible?
Nothing is best. Despite this, Kerberos remains the best access security protocol available today. The protocol is flexible enough to employ stronger encryption algorithms to combat new threats, and if users employ good password-choice guidelines, you shouldn’t have a problem!
What is Kerberos Used For?
It is also an alternative authentication system to SSH, POP, and SMTP.
Comments
Post a Comment